Secure Network Design Micro Segmentation

Use vmware micro segmentation to define and enforce network security policies consistently and operationalize zero trust security for hybrid multi cloud environments.
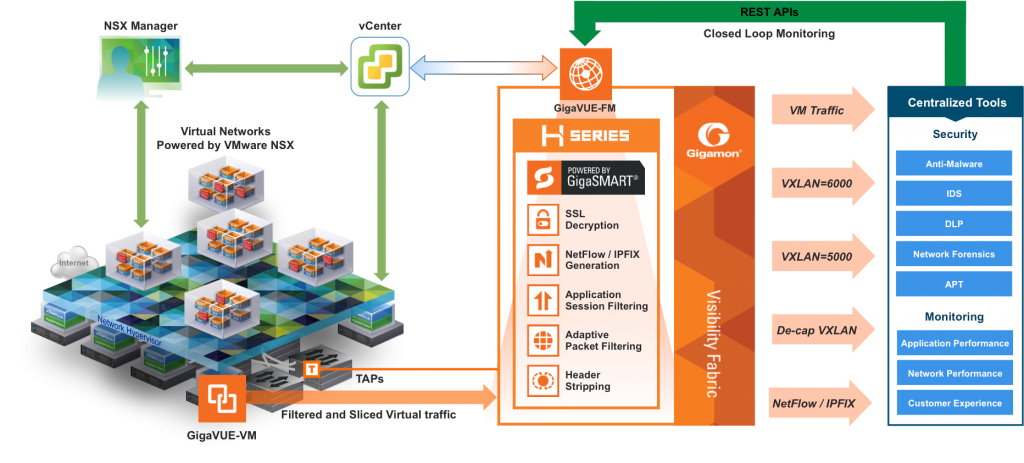
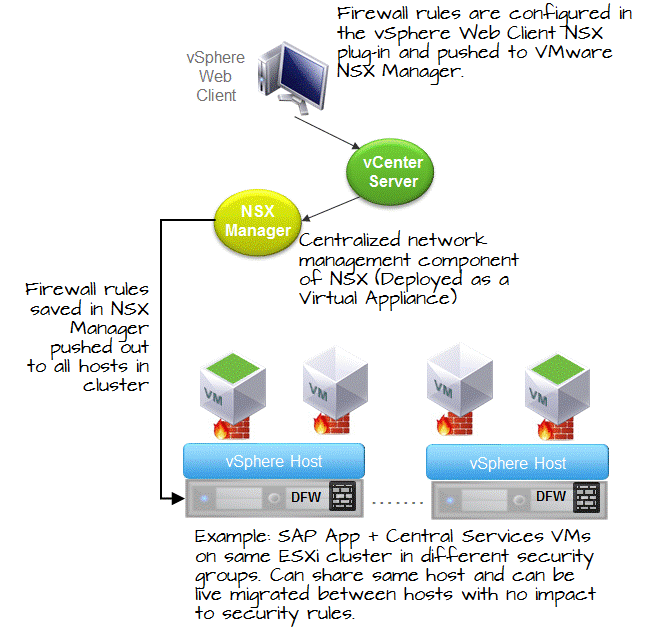
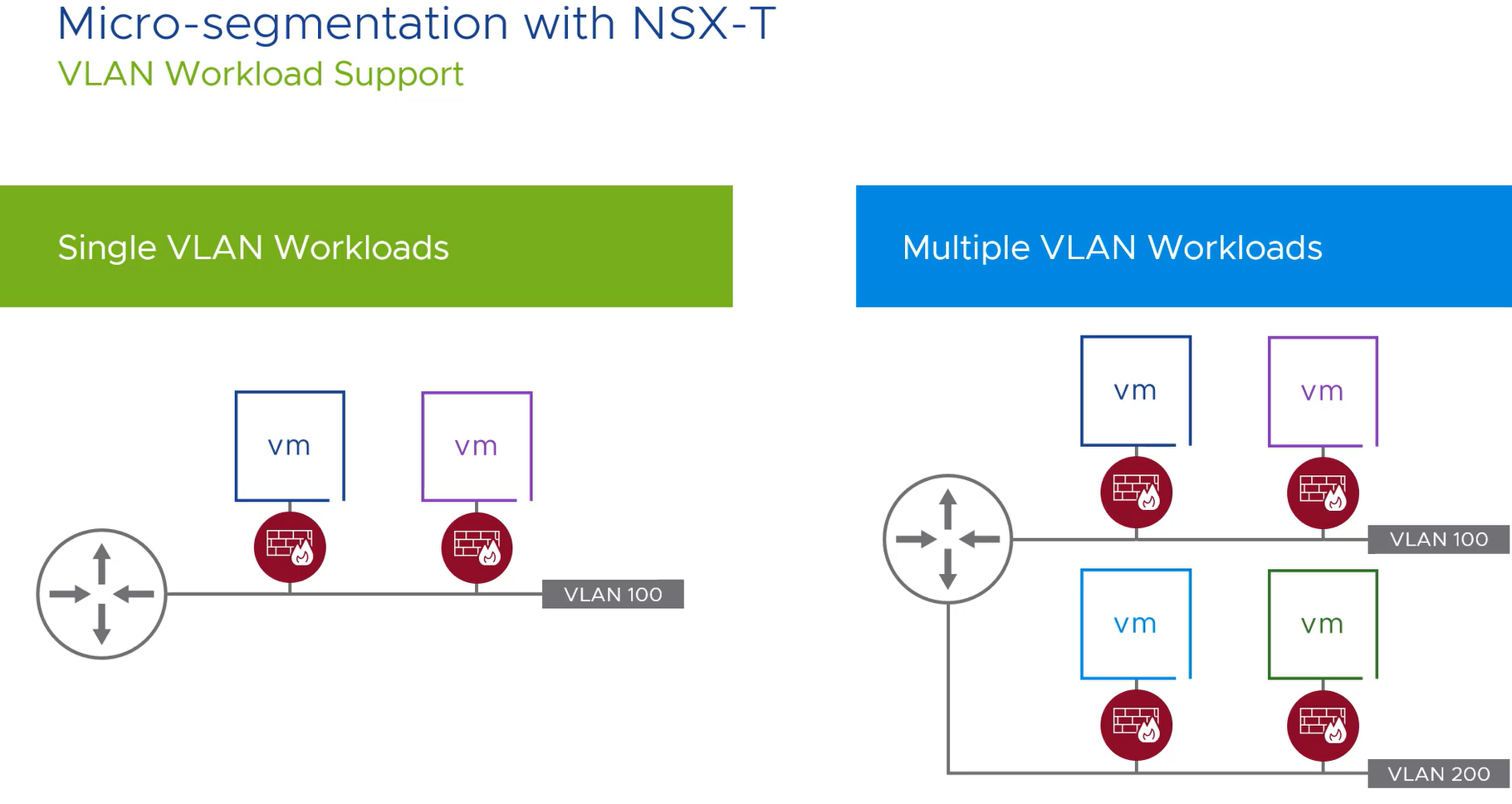
Secure network design micro segmentation. Secure your applications and your seat at the yankees game frank palumbo application security is top of mind for all of our customers. Networks should be segmented including deep in network micro segmentation and real time threat protection end to end encryption monitoring and analytics should be employed. Among other benefits micro segmentation makes network security more granular and thus more effective. Nsx micro segmentation provides a foundational architectural shift to enable topology agnostic distributed security services to applications in the evolving data center.
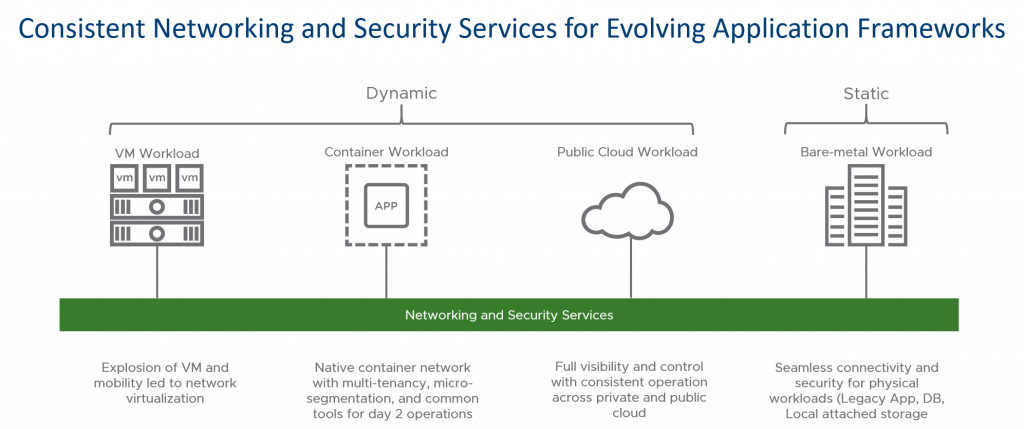
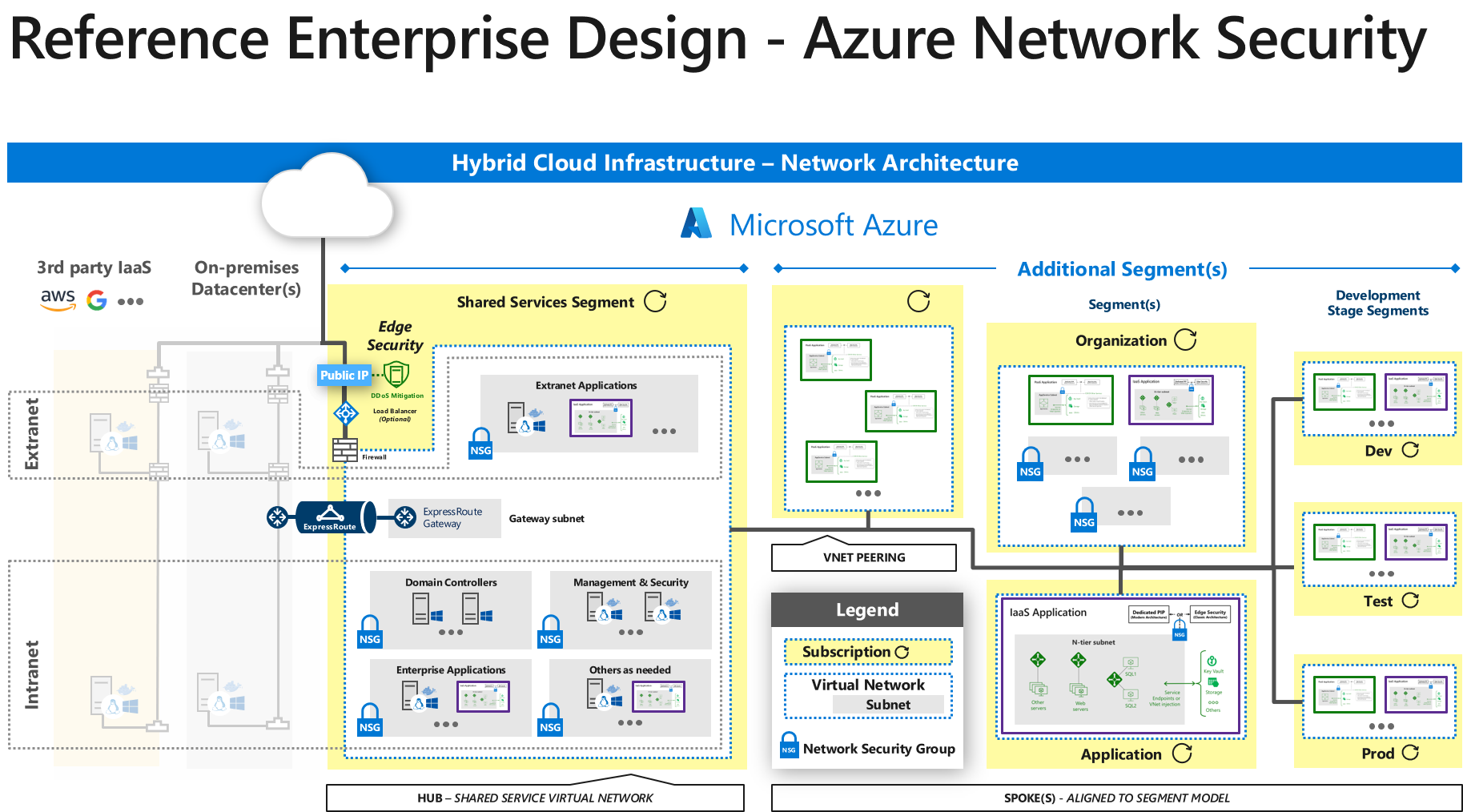
Companies are expanding to the cloud and with the. With nsx application network traffic can be efficiently isolated via micro segmentation regardless of its physical location or underlying network topology. With micro segmentation organizations can move beyond simple centralized network based perimeters to comprehensive and distributed segmentation using software defined micro perimeters. Applications are partitioned to different azure virtual networks vnets and connected using a hub spoke model.
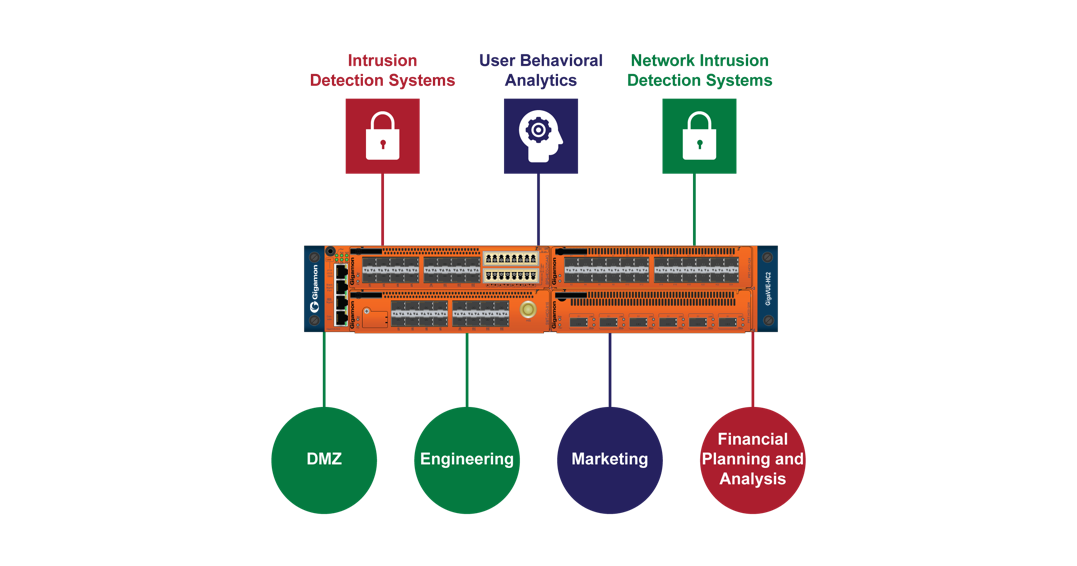
All security functions like intrusion detection systems ids micro segmentation and firewalling can be orchestrated from a single platform. It could be needed across a campus consisting of multiple. Micro segmentation is a method of creating secure zones in data centers and cloud deployments that allow companies to separate workloads and secure them individually. Why network segmentation is essential to creating a secure enterprise environment in this article network segmentation best practices to create secured enterprise environment senior network engineer samuel oppong discusses the reasons why network segmentation as a concept should be employed and implemented by enterprises in the new decade.
A network segmentation strategy developed to enforce security policy in support of an organization s business requirements is typically not limited to a single location. Networking controls can provide critical in pipe controls to enhance visibility and help prevent attackers from moving laterally across the network.